About Tor: Refutations: Deconstructing Arguments Against Tor
Refutations: Deconstructing Arguments Against Tor
[Image: Auguste Doré: The Four Horsemen of the Apocalypse, “borrowed” from here]
Publication date: 2022-04-11
Review
Part 1 of this article covered an overview and pre-history of Tor. Part 1 is an essential background for this continuation of the article.
In Part 2, below, arguments against using Tor are examined.
Mixing with the Riffraff
A common argument against using Tor is:
Why mix with <cite any of the four horsemen of the infopocalypse>
This is often combined with:
If you've got nothing to hide ...
type commentary.
Note: “quote” type representations are being used above, though these are “sample” quotes rather than specifically identified ones. This representation will be used throughout the article to separate the “argument” from responses, which will be in italics. When actual quotes are issued, they will come with citations.
On the first front, this is a fallacious argument, and is easily exposed as follows:
An extremely high percentage of murders drive cars on roads, thus you should not drive a car on a road as you are mixing with murderers.
One can go 'ad nauseam' on this theme: drug dealers use knives (to eat), thus we should ban knives, etc..
Technology is morally neutral, or more correctly “things” don’t have “morals”. How people employ technology to achieve their aims may well not be morally neutral. The fact that murderers drive cars does not mean all car drivers are murderers, nor that car drivers condone murder.
The often associated "nothing to hide" comment is actually a subtle piece of propaganda. The USA slave owning, white men, who had quite a hand in an ongoing genocide against the native population, got many things right in the excellent first 10 amendments of the USA's constitution. These amendments are commonly known as the "bill of rights", which in itself is a misnomer. There is no "bill" of anything. These are ratified elements of the constitution itself.
Amendment IV states:
The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
[An actual quote, the USA constitution, Amendment IV, from Legal Information Institute, Cornell Law School. This is an excellent site for quoting and understanding the USA constitution. It does not block Tor and is very well curated and presented.]
This amendment places a significant burden on law enforcement (an arm of the executive branch of government) and the courts (the core arm of the judicial branch of government). What it says is that one should not be in fear of these two branches of government. They need to cooperate for the courts to issue a warrant, which requires "oath or affirmation" by which one can understand a "basis" for the warrant. Finally, the warrant is constrained by "place, persons or things". The above constraints are able to be challenged by a defence lawyer. Was there a "basis"? How particular were the "place, person or things"?
The amendment is to provide relief from fear of the executive branch's law enforcement. The 4th amendment is in part a response to the "general warrants" which were being issued by representatives of the British colonial government compromising the liberty of the colonists. Battles in USA courts regarding the issuing of warrants close to the line of "general warrants" is a never-ending struggle.
The other subtlety of the "nothing to hide" narrative is that most people who use Tor are actually hiding something; their identity and/or their browsing habits. The insinuation built into "nothing to hide" is best exposed by turning it around. What right does the government, or anyone else for that matter, have to force me to divulge my identity or my browsing history?
Arrest me on a specific charge, or come back with a warrant!
Tor vs. VPN
Another argument is:
Why not use a VPN?
This is actually a good argument until one drills down into it. Tor, the network, is actually a specialized, volunteer run, collection of relays working in partnership, which in effect is a VPN. So, a natural counter to the argument is:
I am !!
At its simplest, a "VPN" is a computer with two network interfaces. On one interface it accepts connections from clients and then uses the other to forward their requests to the desired destination. Because of the change of interface the service (e.g a website) it contacts thinks that the VPN computer is contacting it, not the client. The VPN then re-transmits responses back to clients with the website being none the wiser.
Modern VPNs are more complex, involving not one but many computers linked together to provide the VPN service. A VPN provider will wish to have at least one fault tolerant server in the network vicinity of its core customer base. Similarly, if the customer base wants different points of egress, the place where one’s traffic leaves the VPN network and mixes into "regular" internet traffic, then the VPN provider will host VPN exit points in these locations. To provide a stable service, the VPN provider will lease reliable network bandwidth between the ingress (where the customer joins the VPN) and egress locations. The customer securely connects to the closest ingress service and chooses an egress location. The VPN then tunnels their traffic (securely encrypted) between the ingress and egress locations over the leased network bandwidth interconnection.
[Image: borrowed from an article at smartic.ci]
When using Tor, one’s ingress point, a relay known as a "guard node" is relatively fixed. However, one’s connection is then routed between two more relays, the last of which serves as the egress location. These later two relays are constantly changing. One can choose to limit egress location by geographical region but this is not advised for it concentrates the egress "public" traffic in that region, providing whoever is surveilling that region with more information.
The summary here is that Tor is a VPN, it just works very differently to a commercial VPN, because Tor has different objectives.
The Tor doubter counters with:
But Tor is not run by a for profit entity!
True, but how does this fact add to your argument?
They continue:
Its not as good as a VPN!
Yes in some respects, and no in others. Commercial VPNs are generally faster. This is because, as noted, they invest in high speed connections between the elements of their VPN service. Tor, as a volunteer network, does not have this opportunity. Some Tor relays are faster than others because of hardware or the capacity of the network to which they are connected.
A commercial VPN also makes it much easier to choose the nation or region of egress. This makes it easy to avoid a form of censorship or limited data distribution which is known as geo-IP blocking.
Take the BBC as an example. I like cricket, and they have great "radio" (audio) coverage of cricket, especially when the game is played in the UK. Their funding is from the UK public and the BBC chooses to only allow their coverage of cricket by their premier show "Test Match Special" to be accessed by people connecting from internet addresses in the UK when they are actually covering an international match. This is "geo-IP" blocking, limiting distribution to a geographic area based on the IP address of the connecting computer.
Fair enough, its their product and they are free to distribute it how they wish. With a commercial VPN one can easily convince the BBC that one is "in" the UK and access the content. This is possible, but more problematic with Tor. So, for this use case, a VPN is the superior product.
If, however, one's mission is anonymity preservation, a VPN is an inferior product.
The company that runs the VPN service is subject to the laws of the country in which it is registered. Some of those laws require the retention for some period of logs of its service usage, and these can be requisitioned with a court order. In cases where a government can issue these warrants and gag the company from revealing that the warrant has been issued, one would not even know that one's records had been delivered to the government.
Warrant Canaries
A counter to this "secret warrant" mechanism is known as a warrant canary. This practice gained some notoriety when USA's law enforcement began issuing these types of warrants. They are known as "National Security Letters", or NSLs.
A warrant canary works by an absence of a notice declaring that no warrants have been received for a period of time. When a lack of a new declaration of no warrants received is observed, an observer can assume that a "secret warrant" has been received.
Privacy By Design: Avoiding Warrants by Having No Records
When using Tor+TBB in "default" mode, one makes a connection to three Tor relays in turn before egress. An overview of a Tor "circuit" needs be provided here to assist in seeing what Tor is doing and how that creates a defense against "warrants".
[Image: from the Tor Browser Manual. A more detailed explanation with more detailed graphics will be provided in the technical annex.]
When you start TBB, it starts a local network service known as an "Onion Proxy" (OP). TBB, or any other local network application which supports the type of network connection which the OP provides, can talk to the OP. The OP creates Tor circuits.
Each circuit begins with the OP and connects (by default) to 3 other Tor relays, one at a time, in sequence, to form a complete circuit. Clever use of cryptography ensures that while the OP has a complete understanding of what a circuit is being asked to do, each of the Tor relays involved has a limited understanding. None of the relays are aware of which type of client is connecting through the OP. And none of the relays know both the IP address of the OP and the final destination, usually a website, to which the circuit is being asked to connect.
Each relay knows what it is being asked to do, and is aware of the existence of its neighbours with which it must communicate. However, no relay has a complete understanding of what is happening across the entire circuit.
The first relay knows that your TBB, or some other client, is connecting to it via the OP.
The second relay knows that the first relay is talking to it and that it in turn is talking to a third relay. However, the second relay has no idea that "you", or whichever client, is involved in this.
Finally, the third relay knows the second relay is talking to it and that it has been asked to connect to some web site, which it does, and passes the data back to the second relay. It also has no idea whatsoever about who or what is requesting this connection.
Nowhere in the chain does any one relay know that you are using Tor and to which website you wish to connect. You know. The TBB knows and the OP knows, but that knowledge is limited to your brain and your computer. No entity within the Tor network (the relays) knows this start to end connection, only individual parts of it. Thus, there are no records to be requisitioned by a court, because the records just do not exist.
This is called "privacy by design" as opposed to "privacy by policy (or promise)".
The Department of Defense Origin Argument
The next argument of why not to use Tor is that it was developed by the USA's Department of Defence and that they therefore must be able to "decrypt the traffic" or "deanonymize the users". I assert that the first claim is technically false, for two reasons.
Firstly, the amount of work that has gone into Tor and the tooling produced by the TorProject is so large that the only remaining vestiges of the original work by the Naval Research Labs are the theoretical/academic bases upon which Tor rests. The implementation is wholely different and even the theoretical framework has evolved in the 15 odd years since the NRL gifted their work to the Open Source community and it was embraced by the TorProject. Secondly, the cryptography used by Tor is the best available to the public and that has dramatically changed in the intervening years. It is certainly true that agencies like the NSA have the ability to decrypt communications. However, this is likely expensive in time and/or power consumption, and they must guard against revealing this capability.
However, there is an element of truth to the accusation. There are fundamental, theoretical attacks against Tor, one of which is known as a traffic correlation attack.
Traffic Correlation
If one knows the time it takes for a client to pass through the standard three relay hops when using Tor, and one has surveillance capabilities at the location of the first node and the third node, one can watch the traffic and relate the incoming traffic at the 1st relay (ingress) to the outgoing traffic at the 3rd relay (egress) and thus identify that it is likely coming from whoever "just used" the 1st relay.
The first requirement of knowing the time to traverse the network is somewhat difficult because each relay is run by a volunteer and thus runs on differing hardware using differing operating systems and is connected to different networks. Nonetheless, one could watch traffic going into and out of a relay and learn about its "processing" time. This can be done for all relays if one has a sufficiently large surveillance network.
Despite the fact that the communications between your computer and the first relay are doubly encrypted, as we shall see in the technical annex, the internet addresses of the computers talking (yours and the relay's) are outside of this encryption. Those watching may not understand what is being said, but they are certain who is talking to whom, when and for how long. This is the "metadata" problem in action.
Next the "attacker" needs to understand the topology of the networks between each of the relays and what routes exist between them, and how the intermediate (non-Tor) routers will choose to send their traffic. This is possible, but difficult and not terribly predictable. Even minor delays and thus uncertainties can be incorporated into the calculations for the correlation attack. So, attacks on Tor are possible, though difficult.
However, this same attack method is equally applicable to all commercial VPN providers, thus making the argument moot.
Finally, if one is neither using Tor nor a VPN and just riding bareback on the Internet, the traffic correlation attack is trivial; they just watch you. This is where "mass surveillance" or "pervasive monitoring" comes in. It is trivially easy to monitor tens of millions of people "riding bareback" on the Internet.
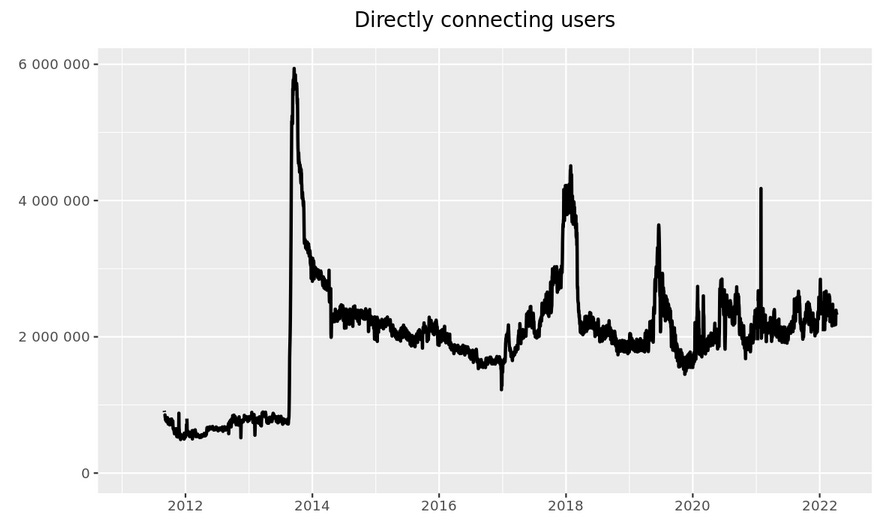
Tor is not "one person connecting to a few relays". Its 2 million people a day connecting to some part of 7 thousand relays and changing their triple-hop-path through those relays every minute or so.
[Image: from Tor Metrics. A history from 2010 of total users of Tor.]
[Image: from Tor Metrics. A total history of participating relays in the Tor network, from 2010. Ignore bridges (the red/orange). They are not covered in this article series.]
Performing a full traffic correlation attack on Tor is very hard which is generally why this is not the chosen form of attack.
The chosen attack is to target individual users of Tor, when this is seen as warranted by law enforcement and condoned by the courts. The take downs of “Silk Road 2.0" and "Playpen" serve as examples of this targeting. USA law enforcement used either non-computer related approaches to identify and gather evidence against their targets, or infected computers of participants in a network to achieve their ends. In the "Playpen" case, law enforcement impounded the server to which people were connecting and installed on it software to infect the computers of people connecting to the server.
One of the sad outcomes of this tactic was that many persons who were obviously sharing child abuse material were not convicted because the infection of their computers amounted to surveillance without a warrant. Personally, I do not believe that prison time is an effective method of assisting people who are excited by child abuse material, but that is another topic all together.
The key point here is that, yes elements of the four horseman brigade use Tor as has already been made clear. However, Tor itself is not the core weakpoint. The weakpoints are the people, and their computers or more broadly their security behaviour. This is known as "OpSec", or Operational Security, in IT security research.
This point cannot be stressed enough. The weakness is not Tor, it is the behaviour of people who use Tor and their lack of "OpSec".
The Sybil Attack
The Sybil Attack is another main theoretical attack against Tor. The attack is to introduce nodes (relays) to the network which are under the control of an attacker. The larger the number of introduced nodes the more influence they have over the network.
A first defence against this is the "guard node", a preferrentially reused first relay. A second defence is that the network is monitored and a sudden increase in nodes can be seen and partially countered.
However, there is a much more pernicious attack and that is a slow introduction of "controlled" nodes which perform completely normally until the attack actually begins. The range of types of attacks which a Sybil Attack can perform on the network is quite wide.
Hans Schouten has published at GitHub an academic article, “Thirteen Years of Tor Attacks” for which he is the 3rd leading author. The article details an extensive history of attacks against the Tor network and classifies those attacks into various categories. The article is deeply researched. I cannot agree with all of the conclusions, but see the work as well motivated and informed.
We can conclude that although a full traffic correlation attack is extremely difficult, Sybil attack variants can perform a collection of smaller scale but targeted attacks which can result in de-anonymization and other defects in Tor's normal operation.
One should expect that a significant degree of the threats posed by these attacks have been responded to and that others remain insufficiently countered. New attack types are actively being researched both in public and in private.
Attack TorProject Itself: Funding
Another argument to question the reliability or independence of the TorProject, and thus its core product the Tor network, is to examine its funders.
The "funding attack" is based on declaring that the USA government is a large funder of TorProject, which is entirely true. TorProject is also funded by civilian "human rights" organisations like the EFF and commercial organisations like Mozilla and many private donors.
TorProject, as a non-profit 501(c), must publish its funding every year. You can find out who is supporting them and draw your own conclusions. Its all there in the 990 reports.
Here are the top three funders for 2020, 2019 and 2018. See Schedule "O" of the 990 form published and submitted to USA's IRS.
RADIO FREE ASIA/OPEN TECHNOLOGY FUND 908,744
INDIVIDUAL DONATIONS 890,353
US STATE DEPT - BUREAU OF DEMOCRACY, HUMAN RIGHTS AND LABOR 752,154
This amounts to just under 58% of total funding (4,400,782 USD).
UNIVERSITY OF PENNSYLVANIA - DEFENSE ADVANCED RESEARCH PROJECTS AGENCY 961,803
SWEDISH INTERNATIONAL DEVELOPMENT COOPERATION AGENCY(SIDA) 749,031
INDIVIDUAL DONATIONS 577,170
This amounts to just over 47% of total funding (4,868,034 USD).
US STATE DEPT - BUREAU OF DEMOCRACY, HUMAN RIGHTS AND LABOR 399,940
RADIO FREE ASIA/OPEN TECHNOLOGY FUND 395,494
NATIONAL SCIENCE FOUNDATION 383,998
This amounts to just over 67% of total funding (1,759,348 USD).
From this we see that Georege Soros (Open Technology Fund), USA State Department, DARPA, SIDA, National Science Foundation and individual donations are key funders in a changing mix. USA government aligned organisations are the dominant funders.
The natural question is, given that Tor is used by the four horseman types, human rights advocates, government operatives, security researchers and just regular people who hate being surveilled, why would the USA/DoD be funding it given these known user demographics? Another natural question is does this funding go towards introducing deficiencies or remedying deficiencies identified?
The natural work of the core development team behind Tor is to either further its capabilities or combat deficiencies. The funding organisations have influence on where efforts are placed. Thus, they can divert attention away from remedying deficiencies and towards new features. This is an effective resource based attack on influencing the priorities of TorProject. There is no escaping this observation.
Another way of looking at this is reminiscent of the NSA's dual mission to perform foreign SIGINT collection and also to deny this capability to foreign actors. In the case of TorProject it is heavily funded by a group of organisations that could be collectively called the Broadcasting Board of Governors (the BBG). The BBG fund the USA's active foreign society influence operations via tools like Voice of America or Radio Free Europe. Essentially this is a civilian arm, amongst others like the National Endowment for Democracy (NED) or the US Agency for International Development (USAID), who provide some support for more clandestine operations by the CIA.
The BBG's TorProject funding is so significant that they are likely to be able to influence prioritization of work by TorProject employees. One can imagine that the Tor network sits in a tricky position for the CIA and its civilian arms. They wish the network to be successful to assist foreign influence operations, but not so successful that it can be used by adversaries.
It is myopic to just cast one's eyes on the CIA. There is a division of responsibility amongst the USA's agencies, for both foreign and domestic purposes. The CIA's job is foreign influence, human intelligence and counter-intelligence. The NSA's (foreign) job is signals intelligence. The DoD's Defence Advanced Research Projects Agency (DARPA) is advancement in technical capabilities.
DARPA's investment in 2019 (close to a million USD) may have been to fund significant improvements that Tor made in its Hidden Services capabilities. This may have pushed effort away from remedying deficiencies. I do not know. It is known that Hidden Services are run by the four horseman types. Does the CIA care about this? I suspect not. They'll flick the problem to the NSA if they get wind of things which concern them. That is the NSA's job.
Foreign intelligence services who rely on Tor for any serious operation are neophytes. The NSA may choose to shuffle SIGINT information via the CIA to the FBI to assist in targeting local intelligence operations. Again, these people are idiots if they are relying on Tor. But, if they have good OpSec skills, Tor may be useful for some limited purposes, particularly deception.
Here we come back to the "rub" of Tor; it is full of a collection of mostly irrelevant "targets", and the observer has to sift amongst them to identify important ones. This takes effort. The signs to take interest in one particular communication will come from human intelligence or metadata analysis which then motivates the use of whichever "magic attacks" the NSA have. Whether these "attacks" are expensive or not, revealing that the NSA has them is expensive.
Nonetheless, it is the NSA's job to monitor Tor and other anonymity type networks, and the VPNs and all of the bareback riders too.
Attack TorProject itself: People
And, say the naysayers,
John Perry Barlow gave speeches to the CIA, so he must be "in on it"
Various other people can be investigated and connections made between them and other organisations. These types of "guilt by association" arguments can show connections in alliegences and this can undermine trust in TorPoject. They inform a potential user of Tor of influences over TorProject and where to look for "hidden hands". I tend to see the funding attack as a more productive approach to revealing these influences, though human influence is relevant.
In the end, Tor is 4 things:
Core infrastructure, such as the Directory Servers
Volunteer run relays
Published source code which runs on these systems
The people who use the network
If you really want to criticize Tor, the single most important thing to analyze is the code and the history of attacks against the network, which I have provided. People and funders come and go. It is the code that runs the network.
If you are interested in "attacking the code" so are many security researchers!!
[Image: a screen shot of one of Tor unofficial repositories on GitHub.]
Security researchers are constantly trying to find weaknesses in Tor and other products produced by TorProject. The researchers at TorProject actively encourage this and engage in academic symposia to engage with this community. Why? Because that is one of the ways by which they increase the security of their products. The whole process actually goes beyond this.
There is a respectful and constructive dialogue between security researchers who are investigating Tor and members of the TorProject community. There have been exceptions to this happy state of affairs. One of the significant attacks against Tor, a Sybil attack, was launched from a USA university without informing TorProject of the attack or what the research outcomes trying to be investigated were.
In the end, they're all researchers looking at a topic and benefit from each others' individual contributions to the body of research. This is a wholesome approach to this topic of security research, not some dastardly, nefarious plot to trick you into using some "backdoored" product.
The core team at TorProject understand the challenge they have, and have been dealing with for over a decade and a half, better than anyone else on our beautiful planet. One of their biggest problems, as identified in the "Thirteen Years of Tor Attacks" article, is their lack of funding. This allows the funding agencies to influence where effort is directed.
This in itself is an attack on the code, via where effort is place on improving/fixing it. How effective this influence is in controlling development, I cannot answer.
The Tor bug tracker is publicly viewable via which one can view priority:
[Image: a screenshot of the Tor bug tracking mechanism.]
Part 3
The article’s next section provides a testimonial as to why the author does use Tor. This is followed by a “view” from how the Internet looks when one uses Tor, and a short discussion of political topics from software freedom to information control.
Sources
Geofence Warrants and the Fourth Amendment, Harvard Law Review, 2021-05-10
Warrant Canary Frequently Asked Questions, Kurt Opsahl, EFF, 2014-04-10
Pervasive Monitoring Is an Attack, Internet Engineering Task Force, 2014-05
Playpen: The Story of the FBI’s Unprecedented and Illegal Hacking Operation, Mark Rumold, EFF, 2016-09-16
Sybil attack, TorProject
Thirteen Years of Tor Attacks, B. Evers, J. Hols, E. Kula, J. Schouten, M. den Toom, R.M. van der Laan, Dr. ir. J.A. Pouwelse (supervisor), Computer Science, Delft University of Technology, The Netherlands, (last updated) 2020-02-27
Reports, TorProject
Video Sources
IETF 88 Technical Plenary: Hardening The Internet, IETF - Internet Engineering Task Force, (streamed live) 2013-11-06
Culture
Ministry of Silly Walks (Monty Python), extracted by Jeff Sherry, youtube channel, uploaded 2016-12-06
Do Not Subscribe: This blog does not issue "notifications" via Substack. Use RSS. The URL is the obvious: https://yesxorno.substack.com/feed .
Following @YesXorNo1 on Twitter is the next best alert mechanism.
Copyright and Licensing
This work is copyright to the blog's author with CC BY-SA 4.0 licensing. Have fun, reuse, remix etc. but give credit and place no further restrictions. Lets build culture.