Published: 2025-03-26
Updated 2025-03-28: Several additional reference articles have been added post publication from good independent journalists/analysts like Snider, Blumethal, Lauria etc..
Update 2025-03-29: An update section was appended containing a brief, and broader, description of security with regard to Signal and computing hardware.
A Tiger Team of Warmongering PR Strategists
That the "principles" (Secretaries of State, Defense, Treasury, the Vice President and Director of National Intelligence) discussed a proposal for, the operational details of and then celebrated the illegal and immoral restart of the US war against Yemen, using the unauthorized Signal secure messaging software, is confirmed.
The confirmation comes via numerous observations beyond the fact that the style of interaction fits the types of statements by the individuals who used their own names or initials. Most significantly, the supposedly, inadvertently added participant into the encrypted text chat group, Editor-in-Chief of The Atlantic Jeffrey Goldberg, checked social media 10 minutes after the time he had been informed that the war restart was meant to begin, to find that:
Explosions were then being heard across Sanaa, the capital city.
US National Security Council spokesman Brian Hughes, when asked about the leak said:
"At this time, the message thread that was reported appears to be authentic, and we are reviewing how an inadvertent number was added to the chain."
"The thread is a demonstration of the deep and thoughtful policy coordination between senior officials."
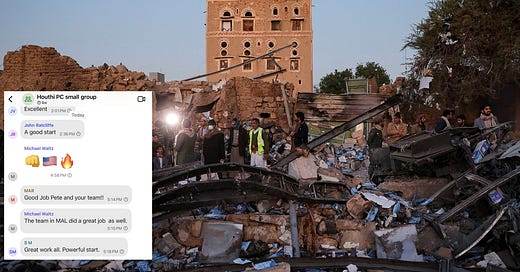
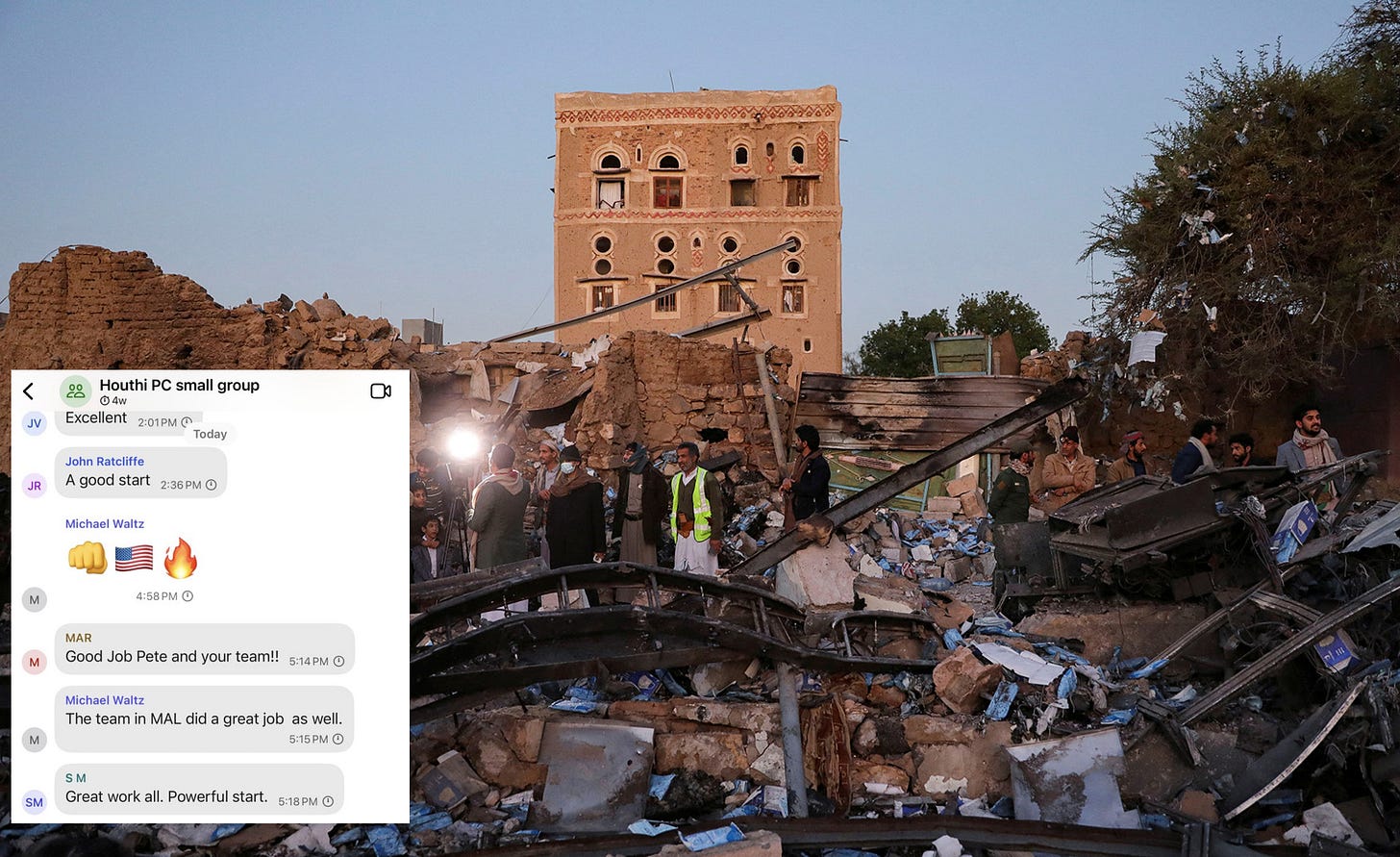
[Goldberg provided three screenshots of the discussion to which he was invited. The emoji's display the "deep and thoughtful" policy coordination.]
US Secretary of Defense Pete Hegseth, when challenged about the leak, responded:
"Nobody was texting war plans, and that's all I have to say about that,"
to which nobody asked, "So, how did Goldberg know when the war would restart?" Hegseth had added mendacity to his stupidity. Confirming his petulance, he later launched the lamest of ad hominem attacks against Goldberg, describing him as a "so called journalist".
Clowns Ruling the Empire
If anyone should be questioned about this total breakdown in operational security, it is surely Director of National Intelligence Tulsi Gabbard. [And yes, she has been roasted in Congress.]
Someone operating her account named "Joe Kent for DNI", Trump’s nominee to run the National Counter-terrorism Center to represent Gabbard in the group. Kent (or someone acting in his stead) did participate, writing "There is nothing time sensitive driving the time line. We’ll have the exact same options in a month." Thus, a Director of National Intelligence's nominee not only did not shut down this out-of-band chat, but participated in it.
We can all imagine the face palming at the NSA over this. Kent’s picture is sure to grace their OpSec tutorials.
Security, Privacy, Convenience
One perennial discussion in secure software systems is the trade off between security, privacy and convenience where the traditional position is: take two. The reason why Signal is the "best in class" for secure communications is that it provides all three. A more informed concept of security, to which we shall come, is required to understand this evaluation.
The question which arises out of the leak is why did these "principles" use Signal at all?
Two answers seem to offer themselves. The first is political.
The current US administration is in conflict with its bureaucracy, having no trust in it. The principles desired a secure communications mechanism which was outside of the purview of their bureaucracy. This raises the question of why they did not choose Meta's WhatsApp? They may not be aware that it and Signal both use the same encrypted communications protocol: Signal's. [And while we're on that, this is because Signal is Free and Open Source Software (FOSS).] The answer to this question probably lies in the Snowden revelations, which informed us that all of the US commercial messaging services, commonly called "Social Media", are in partnership with US intelligence, particularly the NSA. Thus, WhatsApp seemed to the "principles" compromised. It is, but primarily via metadata.
The NSA knows who is texting who, when, for all messages. Obtaining the contents of those messages is a different question. It involves decryption capabilities, which one can be sure US possess. The question is how much effort is required to employ them and how much risk is involved in the employment by revealing capability? But, this takes us away from the topic at hand.
The second answer to "why Signal?" is, convenience. The leaked text chat provides us with the term the principles group use for US government secure communications facilities, "Highside". These systems probably do not fit the pace and mobility of their professional duties. "Highside" is not "convenient".
Privacy
Goldberg informed us how his Signal account was included in the leak. First, US National Security Adviser (yes, that term looks rather silly now) Michael Waltz issued a contact request to Goldberg, which naturally the journalist/editor accepted. Goldberg did not reveal which account sent him the invite to the group text chat. His article covers plenty of arse, and this is its beginning: who sent the invite. He immediately followed, providing a message from Michael Waltz describing the purpose of the group:
“Team – establishing a principles [sic] group for coordination on Houthis, particularly for over the next 72 hours. My deputy Alex Wong is pulling together a tiger team at deputies/agency Chief of Staff level following up from the meeting in the Sit Room this morning for action items and will be sending that out later this evening.”
This group of principles and deputies (reportedly 19 in all), selected by "peacemaker" US President Trump, to coordinate a war is named itself a "tiger team". The tigers are "following up" on an "action item" from a meeting in the "Sit Room ... this morning". That would be coordinating a war in which their primary concern, as Goldberg’s article revealed, is their PR strategy for the US population — how to mislead them as to the motivation for and purpose of the war.
Whoever it was who "pulled together" the membership of the group chat defined its privacy, whether they understood this or not. That Gabbard's deputy Kent did not question this proves that he is totally unfit for his role and needs to go back to information security school where he may find his own picture on the training material.
Convenience can be an enemy of privacy. Onwards, to security.
Security
There are two reasons that Signal is the most secure messaging application.
Its cryptography is best in class, a rolling cipher in which each key is based partially on the previous, which means that no two messages share the same key. Secondly, and most importantly it implements Security by Design instead of Security by Promise.
In a case about 5 years back, Signal were forced to comply with a "National Security Letter" (NSL). These nasty beasts are "business record" requests based on the PATRIOT Act passed after the 9/11 crimes which empower the government to not only demand business records for "national security" but also gag the business from informing anyone that their records are being searched. From this fundamental violation of a speech right, to inform others that the government is suing you for business records, came the practice of the "Warrant Canary". This is further outlined in this newsletter’s Tor series.
In summary, the strategy turns the tables on the government, but at some effort. A monthly notice states that no warrants have been received. When the business stops issuing them, it can be understood that an NSL has been received and that a gagged search is under way.
This is not Trump II era "totalitarianism", but Bush Jr. era totalitarianism which everyone seems to have forgotten about. It was not just the Iraq and Afghan wars which marked Bubba Bush's era in the White House, but some of the the most invasive laws ever to be passed by the US Congress.
But, back to security by design. Signal solves the NSL problem by NOT KEEPING THE RECORDS at all. When dealing with the NSL, those years ago, after complying and then managing to have the gag order lifted, Signal published what they provided in response to the demand for all records for a particular phone number.
Signal provided two records. The datetime at which the device with the phone number had begun using the service, and the datetime when last the device had been in contact with Signal to do something (send a message, if I recall correctly). That is it. Signal does not know anything. It, most importantly, does not have the keys the decrypt the messages. It can't decrypt them. It doesn't care about this. All it cares about is that messages are sent. Once this is achieved, it discards all details of the message transit. These details never hit "storage". They are ephemeral bits in random access memory — in the phones.
Signal does not retain the "metadata", except for those two: first contact, last contact. And neither has personally identifying information in it.
This makes the Signal organisation's infrastructure very poor for surveillance. The surveillor has to intercept data and calculate derived keys at a significant computational cost for every single message. Signal forces the NSA to do the work, and a colossal amount of it.
The other strategy, Security by Promise, is what the NSA wants. Metadata records are kept and siphoned off by the NSA from their official home at the relevant “Social Media” subsidiary. Within the metadata's official home are other metadata which assists the surveillor in their purpose. No NSLs need be issued.
Security by Design
A system like Signal does not meet the needs of a bureaucracy. It cannot be used to later modify or delete messages, or to change who can see them. It is "end to end". The messages start at one and transit to the other, leaving no permanent trace in the infrastructure through which it passes.
Signal's design is anathema to government "secrecy', because government secrecy is about centralized information control. Signal is about de-centralized information control. Signal's security is extremely high. Its privacy, information distribution control, is in the hands of the people who use the service.
The "principles" in Yemen-gate enjoy the power which comes with centralized information control. They do not understand privacy. Joe Kent, the counter-terrorism Czar, representing the Director of National Intelligence, did not have the intelligence to check who had been invited into the group chat before participating in it.
He is an idiot, just like the rest of these warmongering clowns, doing Zionist business with US tax-payer money, and putting the lives of government employees at risk in the process, while murdering Yemeni civilians with US bombs.
Sanctions with Drones
Do you know what really pissed these people off? Ansar Allah, in response the Israeli government armed forces' mass slaughter of Palestinian civilians, is implementing economic sanctions.
Yemen does not possess the leading financial institutions to legislate against Israel's economy. What is has are cheap drones and missiles.
With them it applied, in conformance with the Genocide Convention, a hard sanction against Israel's economy. The US and its "tiger team" members do not like being beaten at their own game, and especially not by brown people wearing sandals. Before long, as many qualified commentators like Col. Daniel Davis have predicted, the US will withdraw with its tail between its legs. The only way to beat Ansar Allah is a land invasion, which would condemn the US even further, sabotage Trump's second term and generate a political backlash in the US.
As Ambassador Chas Freeman noted, Ansar Allah are the effective government of Yemen. Yemen is the only government in the region, and the poorest, which has stood up and supported the Palestinians. Ansar Allah are already regarded as heroes in the Islamic world, for good reason.
They will soon defeat the US, again, and further humiliate the clowns running the Empire.
Update
Even in the informed circles to which I restrict myself to avoid suffering constant blather, discussion of the security of the Signal messaging software has been depressingly poor. People with expertise in other areas and none in cryptography, operating systems, or digital hardware are issuing poorly qualified generalizations about security.
I failed to highlight one extremely important distinction which one must keep in mind when assessing digital security. One security assessment needs to be made for hardware, another for the operating system and a third for the software.
If one has physical access to the hardware, all security is removed, except for the case where the entire device's storage is encrypted with some key (passphrase) without which it will not even start. If this is not the case, there is no security whatsoever.
The next security realm is the opeating system. It has a massive attack surface compared to a piece of software. Once a remote presence is established within the operating system, the security game moves to priviledge escalation. Once that is achieved, all security is defeated.
Mobile phones are the most vulnerable of all general use computing devices. They have no full hardware encryption. They contain within them a privileged section reserved for cellular network access, and therein a basic backdoor for cellular network operators. The operating system, Android, made by Google has its own rat warren of unpublished vulnerabilities.
Signal itself, in its network transport protocols, is extremely secure cryptographically.
A current battle is underway between quantum computing and cryptography. Quantum computing, once stablized and expanded beyond its current limits can trivially defeat most forms of current, agreed as secure, cryptography. It is expected that the NSA and other powerful signals intelligence organisation have achieved this capability. But, revealing this fact is itself dangerous. It is far better that one's adversary is uncertain of one's capabilities.
PostQuantum (PQ) cryptography researchers are quite advanced in their production of cryptographic protocols which defeat the quantum computing capability which the researchers expect the advanced signals intelligence organisations possess.
In summary, Signal is secure in its cryptography against all but the most advanced signals intelligence agencies. The phones on which Signal runs are woefully insecure, unless carefully built by people who understand what they are doing.
People like that do not use mobile phones for anything sensitive.
Postscript
The US government had approved the use of Signal for the “principles” and their deputies (obviously not discussing classified information). This is a vote of confidence in the security of Signal by the NSA which has the academic and professional competence to assess its cryptography and its implementation of it.
or support this work via Buy Me A Coffee or Patreon.
Sources
Escalating an Unwinnable War; Scott Horton / Kyle Anzalone; Antiwar; 2025-03-25
Jeffrey Goldberg's 'War Chat'; Max Blumenthal; Consortium News; 2025-03-25
The Signal Scandal, Carelessness, Revelations, and Hypocrisy; Ted Snider; Antiwar; 2025-03-27
Thoughts On The Trump Team's Signal Chat About Bombing Yemen; Caitlin Johnston; Caitlin's Newsletter; 2025-03-27
It Wasn't a Leak, It was a Devious "Charlie Foxtrot"; Larry C. Johnson; SONAR21; 2025-03-25
The 'Disappearing' War Chat; Joe Lauria; Consortium News; 2025-03-26
Was This 'Leak' Accidental Or Is It Pro-War Psyops?; b.; Moon of Alabama; 2025-03-25
CODEPINK Responds to US Senate McCarthy-Style Attack; Col. Ann Wright; Consortium News; 2025-03-26
US Intelligence Says Iran Is 'Not Building a Nuclear Weapon'; Dave DeCamp; Antiwar; 2025-03-25
Gabbard just issued this. What does that tell us about US direction in the region?
MLAT order from Luxembourg for Signal user data; Signal; 2021-11-02
An example of Signal handling a legal case demanding data
Signal: Best in Class Secure Messaging; YesXorNo; 2025-03-24
The initial article, which contains all of the links to coverage of “Yemen-gate”.
About Tor: What, Why, How and Who is Tor?; YesXorNo; 2022-04-09
Col. Daniel Davis: Is America on the Brink of More Wars?; Alkhorshid interviews Davis; Dialogue Works; 2025-03-24
AMB. Charles Freeman : Will Russia Help Iran if US Attacks?; Napolitano interviews Freeman; Judging Freedom; 2025-03-25
Max Blumenthal : Hegseth Reveals US War Plans.; Napolitano interviews Blumenthal; Judging Freedom; 2025-03-25
Copyleft: CC0




These are diversionary trails hung out to avoid everyone focusing on the point: the Trump admin is not peacemaking but actually re-triggering the WW III that the Biden admin attempted to begin in Ukraine and Gaza.
This then is a diversion. Just like the JFK file dump.
People have to begin to understand the tactics here? Do they need to shoot down some weather balloons next for it to me more obvious?